Improper Input Validation
When software does not validate input properly, an attacker is able to craft the input in a form that is not expected by the rest of the application. This will lead to parts of the system receiving unintended input, which may result in altered control flow, arbitrary control of a resource, or arbitrary code execution.[1]
Challenges covered in this chapter
| Name | Description | Difficulty |
|---|---|---|
Admin Registration |
Register as a user with administrator privileges. |
⭐⭐⭐ |
Deluxe Fraud |
Obtain a Deluxe Membership without paying for it. |
⭐⭐⭐ |
Empty User Registration |
Register a user with an empty email and password. |
⭐⭐ |
Expired Coupon |
Successfully redeem an expired campaign coupon code. |
⭐⭐⭐⭐ |
Mint the Honey Pot |
Mint the Honey Pot NFT by gathering BEEs from the bee haven. |
⭐⭐⭐ |
Missing Encoding |
Retrieve the photo of Bjoern’s cat in "melee combat-mode". |
⭐ |
Payback Time |
Place an order that makes you rich. |
⭐⭐⭐ |
Poison Null Byte |
Bypass a security control with a Poison Null Byte to access a file not meant for your eyes. |
⭐⭐⭐⭐ |
Repetitive Registration |
Follow the DRY principle while registering a user. |
⭐ |
Upload Size |
Upload a file larger than 100 kB. |
⭐⭐⭐ |
Upload Type |
Upload a file that has no .pdf or .zip extension. |
⭐⭐⭐ |
Zero Stars |
Give a devastating zero-star feedback to the store. |
⭐ |
Register as a user with administrator privileges
The Juice Shop does not bother to separate administrative functionality into a deployment unit of its own. Instead, the cheapest solution was chosen by simply leaving the admin features in the web shop itself and (allegedly) demanding a higher level of access to use them.
-
You have to assign the unassignable.
-
Register as an ordinary user to learn what API endpoints are involved in this use case.
-
Think of the simplest possible implementations of a distinction between regular users and administrators.
Obtain a Deluxe Membership without paying for it
The perks that come with a deluxe membership are reserved for paying customers only. There sure seem to be a lot of ways for a potential power user to give their money to juice shop. Perhaps, one of these payment methods could have some unforseen loopholes
-
Look closely at what happens when you attempt to upgrade your account.
-
Go to the payment page for a deluxe membership and try paying through different methods.
-
Try inspecting the requests that go out for each of these methods, using the browser’s developer tools.
-
Maybe playing around with the parameters in these requests could reveal something interesting.
Register a user with an empty email and password
-
Consider intercepting and playing with the request payload.
Successfully redeem an expired campaign coupon code
Apart from the monthly coupon codes found on Twitter the Juice Shop also offered some seasonal special campaign at least once.
-
Try to identify past special event or holiday campaigns of the shop first.
-
Look for clues about the past campaign or holiday event somewhere in the application.
-
Solving this challenge does not require actual time traveling.
Mint the Honey Pot NFT by gathering BEEs from the bee haven
-
Discover NFT wonders among the captivating visual memories.
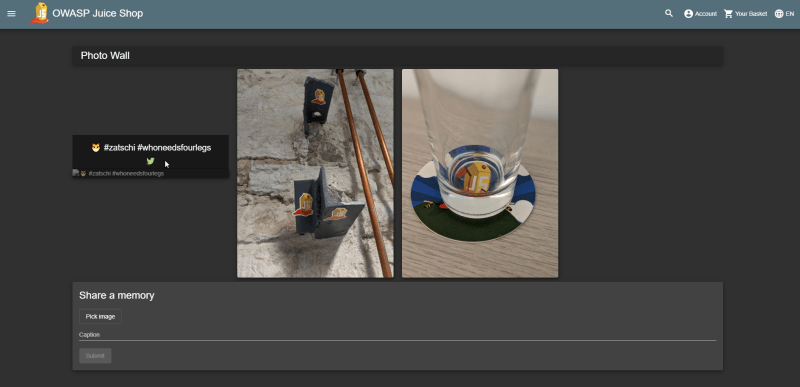
Retrieve the photo of Bjoern’s cat in "melee combat-mode"
Who wouldn’t want to see Bjoern’s cat fighting fiercely with a furry green plush toy?
-
Check the Photo Wall for an image that could not be loaded correctly.
-
You just have to (literally) inspect the problem to understand the basic issue.
-
It can also help to try out the Tweet-button of the entry and observe what happens.
Place an order that makes you rich
It is probably every web shop’s nightmare that customers might figure out away to receive money instead of paying for their purchase.
-
You literally need to make the shop owe you any amount of money.
-
Investigate the shopping basket closely to understand how it prevents you from creating orders that would fulfil the challenge.
Bypass a security control with a Poison Null Byte
By embedding NULL Bytes/characters into applications that do not handle postfix NULL terminators properly, an attacker can exploit a system using techniques such as Local File Inclusion. The Poison Null Byte exploit takes advantage strings with a known length that can contain null bytes, and whether or not the API being attacked uses null terminated strings. By placing a NULL byte in the string at a certain byte, the string will terminate at that point, nulling the rest of the string, such as a file extension.[2]
-
Analyze and tamper with links in the application until you get to an unprotected directory listing.
-
Some files in there are not directly accessible because a security mechanism prevents access.
-
The Poison Null Byte can trick the security mechanism into thinking that the file you want has a valid file type.
-
Depending on the files you try to retrieve you will probably solve "Access a developer’s forgotten backup file", "Access a salesman’s forgotten backup file", "Access a misplaced SIEM signature file, or "Find the hidden easter egg" along the way.
Follow the DRY principle while registering a user
The DRY (Don’t Repeat Yourself) Principle states:
Every piece of knowledge must have a single, unambiguous, authoritative representation within a system.
-
You can solve this by cleverly interacting with the UI or bypassing it altogether.
-
The obvious repetition in the User Registration form is the Repeat Password field.
-
Try to register with either an empty or different value in Repeat Password.
-
You can solve this challenge by cleverly interacting with the UI or bypassing it altogether.
Upload a file larger than 100 kB
The Juice Shop offers its customers the chance to complain about an order that left them unsatisfied. One of the juice bottles might have leaked during transport or maybe the shipment was just two weeks late. To prove their claim, customers are supposed to attach their order confirmation document to the online complaint. To prevent abuse of this functionality, the application only allows file uploads of 100 kB or less.
-
You can attach a small file to the "Complaint" form. Investigate how this upload actually works.
-
First you should try to understand how the file upload is actually handled on the client and server side.
-
With this understanding you need to find a "weak spot" in the right place and have to craft an exploit for it.
Upload a file that has no .pdf or .zip extension
In addition to the maximum file size, the Juice Shop also verifies that the uploaded file is actually a PDF. All other file types are rejected.
-
You can attach a PDF or ZIP file to the "Complaint" form. Investigate how this upload actually works.
-
If you solved the "Upload a file larger than 100 kB" challenge, you should try to apply the same solution here
Give a devastating zero-star feedback to the store
You might have realized that it is not possible to submit customer feedback on the Contact Us screen until you entered a comment and selected a star rating from 1 to 5. This challenge is about tricking the application into accepting feedback with 0 stars.
-
Before you invest time bypassing the API, you might want to play around with the UI a bit.